“Good logging practices are the difference between proactive and reactive security.”
— Jeff Williams (Chief Operating Officer of Apple)
In Today’s world, when cyber threats are increasingly becoming more sophisticated, managing data becomes a major challenge for organizations. Now, companies are leveraging advanced tools and strategies to ensure adequate data management and regulatory compliance.
Log management is one such strategy playing a major role in facilitating the management of large datasets. Organizations are embracing it with open arms, 90% of companies of all sizes are already using or planning to use a log management system.
If you wish to learn more about this approach, then you are at the right place. Working in the IT department, I have answers to all the questions you might have about it, and in this article, I will tell you how it enhances the cybersecurity measures and overall system performance of our company.
Let’s get started!
The Role of Log Management in Cybersecurity
What would you expect from an ideal cybersecurity system? If I had to answer this question, I would say that it should offer continuous monitoring, real-time detection, threat intelligence, compliance and reporting, incident response, data protection, and audit trails for forensic and incident investigation.
But is there anything efficient enough to handle all this? Well yes, log management delivers it all and plays a pivotal role in monitoring, detecting, and responding to security incidents by facilitating all the above-mentioned functions.
If you are looking for an effective log management system, the team at Logmanager can offer you unmatched IT observability and security with their expert-infused technology and highly reliable systems.
INTERESTING TIDBIT
Log data is capable of occupying nearly terabytes of data per day in the case of large organizations.
Detecting and Preventing Cyber Threats
Log management offers a proactive approach to security. Like a camera working 24/7, it offers continuous monitoring. Now if any suspicious activity is recorded or identified by that camera, It will report this incident to the organization in seconds or even better, would flag these inconsistencies on its own.
It also records IP addresses to pinpoint the source of potential attacks or trace who is accessing the system and from where, providing organizations with valuable insight into the source of network activity.
Meeting Compliance and Regulatory Requirements
You might be aware that every industry is required to adhere to certain regulatory compliance. When it comes to IT departments, standards like SOX, GDPR, PCI DSS, and HIPAA, mandate organizations to store logs.
Advanced log management tools can take this burden off organizations by automatically managing the retention of logs based on the latest guidelines. It is also efficient in maintaining audit trails, ensuring accountability and traceability.
Improving Incident Response Times
As I mentioned before, this is a proactive approach that delivers real-time monitoring and faster threat detection. It is obvious that this immediate detection would result in a quicker response. Hence, allowing response teams to investigate and mitigate issues at an early stage, minimizing damage and greater risks.

Enhancing System Performance and Reliability
From all the functions of log management, I’ve mentioned till now, it must have become clear that it plays a crucial role in enhancing the overall performance and reliability of the system
All the features offered by it allow our organization to identify bottlenecks, optimize resources, and resolve issues quickly. Even as we grow and scale, this robust system will help us ensure that our system remains responsive and secure.
Strengthening Long-Term Security Strategies
Working in an environment where I get to witness the efficiency of these systems on a regular basis, I can say that log management is a cornerstone for a long-term security strategy. The assistance it provides to address security challenges, reduce risks, and improve incident response is of significant value for organizations. As the trends continue to evolve, log management will help companies ensure a resilient and adaptable security posture.
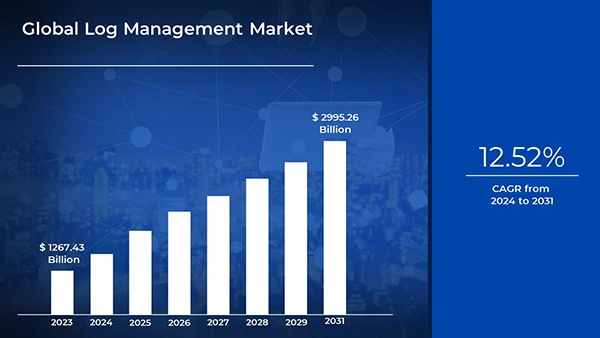
The global log market is expected to value at $2995.26 billion in 2031, compared to $1267.43 billion in 2023, growing at a CAGR of 12.52% in the forecast period.
Building a Culture of Security Awareness
Integrating log management also helped us foster a culture of security awareness in our organization. It is essential for everyone involved in the process to be aware of the impact their actions have on the organization. So, we leveraged log training, and empowered our employees, boosting the overall security posture.
Final Words
I hope this article helped you understand the impact of log management on businesses and the crucial role it plays in data management. From providing an efficient system for threat detection to enhancing incident response, log management offers a holistic approach. Which is being preferred by an increasing percentage of organizations to help manage the gazillion amounts of data they deal with.