In 2022, there were 5.5 billion malware attacks, and 560,000 new pieces of malware were sent every 24 hours. Trojan horses account for 58% of all malware attacks. With such risk, it is indispensable for businesses to count on cybersecurity.
Cybersecurity here is not only about having an antivirus or a firewall. On the enterprise level, the security infrastructure is built on a massive scale. Since businesses deal with a lot of personal consumer data, any weakness in their security may lead to huge legal and ethical implications, which may also lead to ceasing your operations.
Hence, we have curated this effective guide to help you get a basic idea of how a cybersecurity strategy is made for a business. Also, learn about YouTube Brings Video Quality Settings for Shorts by reading this article.
Identify and Assess Potential Vulnerabilities
Taking one step at a time, you must start with identifying the areas where the potential of any cybercrime is the highest. Furthermore, if you are not able to maintain your in-house SOC, you can outsource them to anyone with effective customizable managed SOC services quality.
Coming back to the point, this is how you identify the vulnerabilities:
- Asset Inventory: All the assets such as hardware, software, networks, etc. must be monitored and recorded. Then, the sensitivity of each asset must be determined.
- Threat Assessment: Threats can be identified as internal and external threats. Pointing them out and taking action against them is necessary.
- Vulnerability Scanning: For further scanning, you can run both automated and manual verification of the whole tech infrastructure at your workplace.
If you outsource this requirement to some service, they run specialized techniques and procedures that help in figuring out these vulnerabilities.
Implement Strong Access Controls
Your business systems must be accessed by the concerned professional only, as they accommodate numerous sensitive information. Here’s how you can ensure the access:
- Multi-Factor Authentication: You must start by introducing various authentication options. For instance, use biometrics like fingerprints, facial recognition, etc. Along with that, OTP is another great option.
- Password Policies: Passwords must be set according to the recommendations that consist of a lower case, upper care, numerical, and special character, and must be at least 8 characters long. Along with that, make it mandatory to update passwords at regular intervals.
- Role-Based Access Control: Only the professional concerned with the subject must get access to the systems. Any interference from outsiders must be avoided as much as possible.
- Access Reviews: Regularly keep on verifying if the access is provided to the right person or not. If there is any person with illogical access, revoke it.
- Secure Remote Access: Introduce security infrastructure for those who are accessing the data remotely. Use VPNs, proxies, etc.
Educate and Train Employees
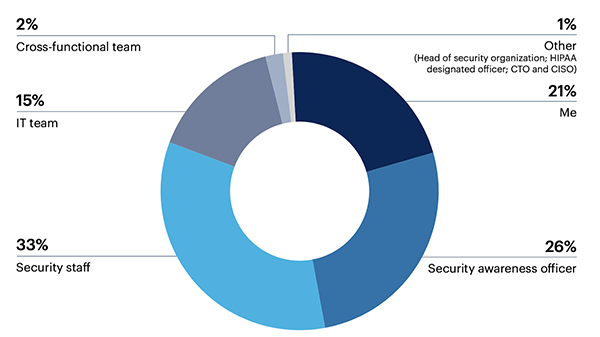
This pie chart by Gartner shows who, in a firm, is primarily responsible for your organization’s security awareness and training program. However, here we are discussing how education and training of employees must be done:
- Needs Assessment: Not everyone is a master at cybersecurity. A majority of employees just care about their task and their completion. Hence, it must be ensured that each department assesses and practices cybersecurity.
- Mandatory Training: The training must be mandatory for everyone. It must cover all departments to keep their respective operations safe. Also, the cybersecurity plan must cover topics like phishing, social engineering, password security, data privacy, and incident response.
- Role-Specific Training: The curriculum you follow must be unique and tailored according to the job roles you are offering. Each employee must be aware of what to do or what not to do in their respective job field.
- Phishing Simulations: Remember how there used to be a fire drill at schools to practice the situation when there’s a real situation like that? Phishing simulation is just the same thing. You intentionally send some emails that look suspicious and need to be avoided from the use. The intention here is to make employees able to understand what mail to avoid.
- Gamification: 95% of employees prefer to work for companies that use gamification. If you can manage to gamify the whole process of training, nothing can get better than this.
Develop and Enforce Security Policies
Well, if you have read the article with attention, developing security policies is pretty much straightforward. Here’s a concise guide on how to do so:
- Identify Critical Assets and Conduct Risk Assessment: Start by finding out the critical assets that your business cannot afford to lose. Evaluate what can go wrong with them and their vulnerabilities.
- Develop Comprehensive Policies: With respect to the threats and dangers, create guidelines and regulations that can counter them. For instance, mandate password updates, data privacy, incident reporting, etc.
- Communicate and Invest in Employee Training: It is pertinent to build a proper communication channel with your employees. Ask if they are facing any problems or if is there any suspicious data loss. Consider investing in employee training so they are self-dependent in keeping their systems safe.
- Implement Technical Controls: Technical controls are simple tools that help in keeping everything safe. For instance, passwords, encryption, firewalls, etc.
- Monitor Execution: Make sure that the regulations made are effectively followed and implemented within the premises.
Continuously Monitor and Improve
Lastly, cybersecurity is necessary and unavoidable. Hence, we made this post to educate you on how you can make your enterprise free from maximum potential threats. Also, it is taking these steps alone is not enough. You must keep an eye on these practices and ensure they are followed all the way.